- En
- Fr
- عربي
Constructing Virtual Identities: The Process of Personal Gatekeeping
Introduction
Amy likes to go on long treks, dine out and play the violin. Her friends and family are aware of this; her “friends” on Facebook and her “followers” on Twitter know this, too, because of the pictures and status messages she posts. But, Amy also enjoys reading young-adult fiction before bed and this is a piece of information she does not acknowledge on her various online social networks. What decision making process does Amy go through when she posts certain things on different social media platforms? What happens during this process? How do Amy and millions of other social networking users choose to reduce the many elements that form an identity to a few that can be seen by others?
It can be said that people assume the task of maintaining social identities when they create a digital presence on social media websites like Facebook, Twitter, LinkedIn or Instagram. The websites vary in purpose and it is inferred that the user may create multiple identities to tailor the type of response they hope to attract from the different social media platforms. The many facets of the personality travel through cognitive channels where they are narrowed down to 140 characters, status updates or photos to give a fellow user insight to the creator’s personality.
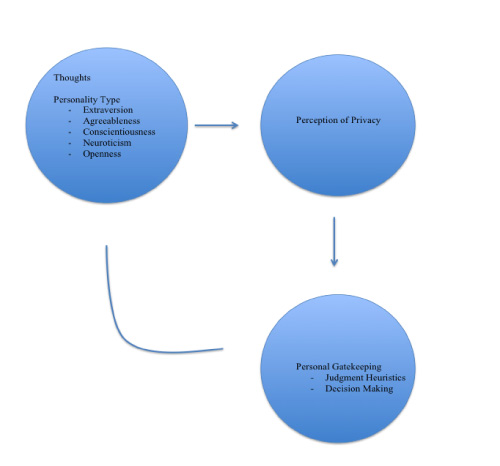
This theory investigates the cognitive processes that factor in the forging of virtual identities in social media. The theoretical framework upon which this study is built on is a combination of intrapersonal communication and Gatekeeping theory. In addition, the theory incorporates the concept of Altman’s theory of privacy and Digman’s Five-Factor model. Identities are created through a manner of additions and deletions; it can be assumed that identities are refined by numerous personal and social factors, which lead to the end result that is virtual identity.
The identity we decide to present on social media goes through a process of decision-making. The individual may choose to reveal a specific aspect of their personality while choosing to omit others. We theorize that the decision making process may vary in strength by the individual’s personality and perception of privacy; the outcome of which is the individual’s virtual identity.
I -THEORY
We present a theory that combines elements of intrapersonal communication, personality traits, privacy and judgment heuristics that can influence the way an individual establishes their identity in the virtual world; these factors can also cause an impact on the quality and quantity of information that the individual chooses to publish on their social website. Furthermore, this section will investigate the decision making process that occurs at the personal level to explain the presentation of virtual identities.
1-Intrapersonal Communication
Intrapersonal communication is essentially a conversation that an individual has with oneself. It is the “physiological and psychological processing of messages” to create meaning (Vocate, 1994, p. 5). Similar to communication that one may have with another individual, the self engages in conversation with itself to process thoughts, feelings and emotions. This is an area that not only interprets cognitive messages, but also creates new messages that can be shared with others.
Mokros (1996) writes, “the construct, intrapersonal relationships, conceptualizes the individual as a system of relationships involved with one another” (p. 198). The self is comprised of multiple selves that are in constant conversation with one another through self-thinking, questioning and criticizing (Mokros, 1996). This process is at the center of our theory. Ideas enter the mind where they pass through different channels and may be challenged. The result of this process are the ideas we form to express our identities. This process decides the aspect of the multiple selves that we share with others. For example, a married, football loving graduate student may choose to display only his academic interests on his LinkedIn page. This decision to display one aspect of our multiple selves is how we present ourselves to others.
This theory illustrates how individuals go through a process of interpreting messages privately to engage in public discussion through social media. The purpose of social media use is endless; they may be for expanding relationships, finding love interests or even cathartic spaces to discuss personal thoughts. This theory demonstrates how the multiple aspects of the self are presented through different social media platforms and the factors that lead to the specific bits of information that people share with others.
2- Five-Factor Personality Model
In addition to cognitive processes, there are multiple factors, that influence the creation of virtual identity, and one such factor is personality. Gender, age, education and other aspects of the self may also contribute to the virtual identity. For example a younger individual may be more active on social media versus traditional forms of communication that an older person is more accustomed to.
While the Five-Factor model (Digman, 1990) has been used widely in the field of psychology, there has been a lack of its presence in the field of mass communication, especially its impact on social media users. This theory employs the Five-Factor Model which is a hierarchical model that organizes personality traits into five distinct categories – extraversion, neuroticism, openness to experiences, agreeableness, and conscientiousness – with the decision-making processes that a user undergoes when they choose to publish information on their social networking websites. This model is used for its ability to understand personality as a common human structure (McCrae & Costa, 1997). The hypothesized universality of this model will look at personality factors to explain the way an individual presents their identity. The above-mentioned traits can impact the way an individual presents their identity to others via social media. For example an extraverted personality may be more inclined to share personal information on their social media page than an introverted personality (Correa, Hinsley & Zuniga, 2010).
3- Privacy
The perception of privacy may be deemed as an important element in the use of social media and can affect the way the user represents him/herself on it. The protection of the user’s private information, be it their basic information, photo or their comments, become crucial as their virtual connections between people expand with each contribution to the website. A million connections are made every day on numerous social websites around the world, which has caused the administrators to ensure that the users involved in these networking sites maintain a sense of safety and security.
Irwin Altman writes, “privacy is the selective control of access to the self” (Altman, 1975, p. 24.) He adds that over a period of time, an individual may respond to changes in their environment by limiting or expanding their interaction with their group (Altman, 1975). We use this theory as a guiding tool by saying that privacy may affect the manner in which the user controls their virtual environment; the perception of privacy may cause the user to control his environment and allow/deny access to certain types of information on the social website. The various states of privacy that run through social websites’ privacy policies and the manner in which they affect user’s attitudes tie closely with Westin’s theory of privacy. Westin outlines four main states of privacy that individuals adhere to - personal autonomy, emotional release, self-evaluation, and limited and protected communication (Westin, 1967, p. 10). Personal autonomy highlights the connection between the user’s sense of individuality and the level of privacy they perceive as the least threatening to their inner core of information (Westin, 1967, p. 10). Registered users on social websites hold a distinctive notion of this individuality that cause them to change their privacy settings in accordance with their perception of threat to their inner “core” (Westin, 1967, p. 10). The connotation is that the self is the one who decides when information is released to the public forum; the user has absolute control over the privacy controls. We theorize that the greater the level of perceived privacy, the more the user is engaged with social media use.
It can be assumed that with the rise in security risks on social websites, the administrators have become increasingly cautious in providing users with options to control their privacy settings that can in turn influence the quality and quantity of information that is put forth by the user.
4- Gatekeeping Theory
Shoemaker and Vos define gatekeeping as “the process of culling and crafting countless bits of information into the limited number of messages that reach people each day” (2009, p. 1) which we believe can be applied on a micro-level under the name ‘personal gatekeeping.’ The individual goes through a process of narrowing the million elements of their self to a select few that the individual chooses to present as their virtual self. It can be said that the very act of following a user on Twitter or “friending” a person on Facebook may be a sign of gatekeeping (Wittkower, 2010, p. 204) as this creates an official sense of association; the very act of allowing a person access to information that is otherwise private symbolizes a sense of perceived control on that user. The user may find the need to alter the information that is presented to their audience as a response to perceived risks to their privacy, hence doubling as gatekeeper. The user now has more control on the information that they choose to put up targeting specific audiences (every major social website has privacy controls that can prevent outsiders from access to their information if they choose it). This also draws attention to the fact that the user has control to access the information they choose as well (on Facebook, the user may change their privacy settings to allow posts only from certain people to appear on their News Feed). In the essay “Gatekeeper, Moderator, Synthesizer,” Butera cites the example of the social website Buddytown that was an exclusive social website that only allowed users to join if they received invites. This website lacked any form of privacy control which meant that any information posted on it by the users was accessible to everyone which meant there was no private information or way to communicate privately to other members on the website. This led to its eventual demise, as individuals tend to join social websites to “privately” and effectively communicate their personal information in a safe and trusted environment.
Altman places the process of social interaction at the heart of his theory (Altman, 1975) that can be applied in this study as well by theorizing that there are certain personal and social factors which shape the information being created, processed and then sent out into the user’s virtual world. These factors could be the virtual community where the user’s “friends” or “followers” function on a set of norms that have been established and accepted by the community as a whole. For example, a user registered on a social website that caters to academia may limit their interests to academic literature and academic events as that is the established norm in the user’s community. Conversely, a person using Facebook for personal reasons may post personal photos, hobbies and favorite movies that may be the norm in his community. Then, there is the importance of judgment heuristics that influence the manner in which the user presents their virtual self. Shoemaker and Vos (2009) define judgment heuristics as “rules of thumb” (p. 37) that are applied without conscious effort. The gatekeeper is said to go through this process, which then affects their decisions about the quantity and quality of information that passes these gates (p. 37). In a similar way, the user also uses judgment heuristics to categorize information they present based on the information they receive on their virtual platform. Information that is presented by the user on their virtual platform may not go through rigorous fact-checking or decision-making processes; it may simply be a judgment on the part of the user to put that information out there. For example, Mike writes that he’s hungry and there’s nothing in his fridge - Mike may not have put a lot of thought into it, it may simply be that Mike is normalized to similar updates from his friends.
In conclusion, we theorize that there are multiple factors that influence the virtual identity creation process, namely, intrapersonal communication, personality type and privacy. The self goes through a decision-making process that affects the quality and quantity of information that is then presented on their social media platform. Identity is a process that may be influenced by cognitive and social factors. Identity creation is an area of interest that has been explored in depth by scholars primarily in the field of psychology. However over the past decade, there has been a boom in social media websites that have allowed for individuals to interact virtually and create online identities. Similar to identity creation, we argue that the construction of a virtual identity is a process where the individual undergoes a cognitive process to present an identity on social media. Depending on the platform and their target audience, an individual may choose to share or withhold certain information.
5- Hypotheses:
H1: Introverted individuals are more likely to seek out social media use than extroverted individuals.
H2: An individual who perceives a social networking site as more private will use social media more frequently.
H3: An introverted individual who perceives social media as private will use social networking sites more than extroverted individuals.
H4: An introverted individual may allow their audience more access to personal information posted online than an extroverted individual.
6- Assumptions:
We present this theoretical model on the assumption that social media will be widely used in the future; and, each of these social media platforms will be distinctly different from one another with a unique purpose that serve the registered users. In addition, we are basing this theoretical model on the limitations of Digman’s Five-Factor Model that every individual will fit this model; perhaps there are other extensions of personality that can also be explored in relation to creation of virtual identity.
II-DISCUSSION
As we stated above, there are multiple factors that can lead to the creation of virtual identity. We look at four main ones in particular – interpersonal behavior, Five-Factor Model, perception of privacy and Gatekeeping theory. We use these concepts, which have been explored in great depth in relation to traditional media and expand these theories to include new media. We use different criterions to evaluate our theory. They are as follows:
1- Explanatory power
This theoretical model draws from different theories to create the process of virtual identity. The theory doesn’t solely elaborate on prior literature. Instead, it borrows and builds upon different disciplines to create a new theory. It attempts to tie the concepts of privacy, personality traits and gatekeeping to understand the variations in the virtual identities that are created by the users. The content that is available to the intended audience on a specific social networking site is presented after a process of decision making and judgments that may arise from the user’s personality, perception of privacy and information they deem as important or valuable. Using survey methodology we can test the hypotheses that back the theory to test users’ perception of privacy and gauge their personality traits proposed by Digman.
2- Scope
The paper will extend the previous scope of this theory into understanding the creation of virtual identities that stem from the users’ personality traits. When a user interacts on social media they are exposed to a large quantity of information that they may wish to share to their intended audience. They will then engage in a process of decision making which allows them to choose only a specific piece of information that they will publish on their platform. Kahneman, Slovic and Tversky (1982) write that there are certain judgmental heuristics that people employ when they are faced with a decision. Shoemaker and Vos (2009) argue that the gatekeepers’ judgment heuristics can affect the decisions that allow information to pass through a gate. Similarly, there are personal and social factors that can affect the users’ cognitive judgments about allowing information to pass through the gates and on to their social networks. For example, if the user is a member of a social network that targets professionals then they may refrain from posting personal information and instead decide to choose information that is professional and perhaps, impersonal in nature.
While this allows us to see information passing through the gates in traditional media, it has not been studied extensively in relation to new media. Another point to consider is that it is also applied on the macro-level of news organizations. We seek to understand this theory on a micro-level, a more personal level of gatekeeping that can accommodate social networking sites and the users’ practices of selecting information for their intended audiences.
To be more specific, the paper strives to condense the Gatekeeping theory proposed to an individual level - personal gatekeeping - where the user narrows the billions of information that is available to them to a few that they publish online. This choice is not only affected by their individual personality traits but also by their perception of privacy.
3- Predictive Power
Not every individual is alike Therefore, social networking use varies. An individual who may be high in introversion and high in neuroticism may potentially seek social networking sites more than an extraverted individual low in neuroticism. Similarly, privacy changes on social networking sites lead to uneasiness about who may have access to personal information. When the perception of privacy is low, an individual may not be as inclined to share personal information for uncertainty of who may have access to that information.
This theory serves to explain the possible relationship between personality, privacy and social networking use. It draws upon work from various disciplines including media studies and social psychology.
4- Falsifiability
This theory cannot explain every aspect of a users’ behavior on social networking use but it attempts to explain personal factors that may influence how much and what type of information an individual decides to share with friends or followers. This theory can be tested using quantitative survey methodology which can evaluate the users’ personality type and their perception of privacy which can influence their virtual identity. This theory works at the micro level of analysis. It deals with the cognitive and social processes that may influence the way an individual interacts with other users on a virtual platform. While it may explain social networking use in general, it focuses specifically on the individual user.
5- Parsimony
We believe that this theory is parsimonious in that it addresses the creation of virtual identities by a fairly simple combination of personality traits, intrapersonal communication, privacy and decision-making. These concepts impact each other in a pretty straightforward manner, which can be seen in Fig. 1.
6- Internal Consistency
Digman’s Five-Factor model can be considered mutually exclusive; therefore a person who is categorized as introverted cannot be categorized as extroverted. Similarly, a person who considers a certain piece of information as private will not consider that public information.
7- Heuristic Provocativeness
This study expands on previous literature, and our theory generates new hypotheses, which addresses new media. We link the concepts of privacy, Gatekeeping, interpersonal behavior and personality traits to explore a new avenue which have not been explored in terms of new media.
To sum up, virtual identity creation is a process that explores personality, privacy and personal gatekeeping. The aim of this theory is to better understand the cognitive and social processes that influence the type of information that individuals choose to share with friends or followers (audiences). This is a new theory that expands knowledge previously focused on traditional media to the area of social networks and virtual identities. While our theory focuses on the individual, future research could investigate the cognitive processes that occur during social networking use on a more macro level of analysis.
References
Altman, Irwin. (1975)."The environment and social behavior". Monterey, CA: Brooks/Cole.
Correa, T., Hinsley, A., & Zuniga, H. (2010). "Who interacts on the Web?: The intersection of users’ personality and social media use". Computers in Human Behavior, 26, 247-253.
Digman, J. (1990). "Personality structure: Emergence of the Five-Factor Model". Annual Review Psychology, 41, 417-440.
Kahneman, D., Slovic, P. & Tversky, A. (Eds). (1982). "Judgment under uncertainty: heuristics and biases". Cambridge: Cambridge University Press.
McCrae, R. R., & Costa, P. T. (1997). "Personality trait structure as a human universal". American psychologist, 52(5), 509-516.
Mokros, H. (Ed.). (2003)."Identity Matters". Cresskill, NJ: Hampton Press.
Shoemaker, P & Vos, T. (2009)."Gatekeeping Theory". London: Routledge.
Vocate, D. (Ed). (1994)."Intrapersonal communication: different voices, different minds".
Hillsdale, NJ: Lawrence Erlbaum Associates.
Westin, A. (1967). "Privacy and Freedom". The Bodley Head Ltd: London, UK.
Wittkower, D. (Ed.). (2010). "Facebook and Philosophy: What's on Your Mind"? (Vol. 50).
Chicago: Open Court Publishing.
تكوين هويات رقمية: عملية حراسة البوابات الإعلامية الشخصية
يمكن المجادلة بالقول إن وسائل الإعلام التقليدية تم استكشافها من كل الزوايا تقريباً مما أدى إلى ظهور عدة نظريات في مجال التواصل. إلا أنه مع التفجر الكبير للمواقع الاجتماعية خلال العقد الماضي برزت بعض الثغرات اللغوية المهمة المتعلقة بوسائل الإعلام الحديثة. يسعى هذا المقال إلى ملء الفراغ عبر ابتكار نموذج نظري لفهم عملية خلق هويات رقمية يمكن أن يُنظر إليها كامتداد للهوية الفردية. ويجمع المقال أيضاً مفاهيم من السلوكيات الخاصة بالعلاقات بين الأشخاص وعناصر الشخصية الخمسة ونظرية حراسة البوابات الإعلامية والخصوصية ويبتكر عبارة حراسة البوابات الإعلامية الشخصية لفهم عملية خلق الهوية الرقمية.